Considering the prevalence of data breaches and inadvertent exposure of personally identifiable information (PII), organizations are starting to strategically embrace privacy-enhancing technologies (PETs) in an effort to bolster privacy protections for data collected from users who have provided consent to share their personal information.
Some companies are using PETs to complement or augment existing privacy protocols, such as consent banners. In effect, the advent of PETs is allowing organizations to expand their privacy protocols and move away from a binary approach to a multi-layer, dynamic approach.
This is something Didomi is very familiar with: We help organizations customize user privacy experiences in accordance with all regulations, environments, frameworks, and standards. Didomi has collaborated with thousands of companies across the globe to address consent and user privacy preferences, monitor vendor and tracker activity, and reduce overall compliance risk.
In this article, we take a look at what PETs are, look at some examples along with their benefits and drawbacks, and what they mean for digital marketing as a whole.
What are privacy enhancing technologies (PETs)?
By way of background, PETs are technologies, strategies, and techniques designed to help protect the privacy of an individual’s PII when that individual has provided their consent to have personal information processed, transferred, and stored by an organization.
The overarching objective of PETs is to help ensure that, once an organization has obtained consent from individuals and collects their personal data, that information is kept private and protected from inadvertent disclosure, even while organizations are utilizing that data for data analysis and/or collaboration.
Consent management as a PET
As a recognized leader in consent management and data privacy, Didomi has been at the epicenter of observing the evolution of Consent Management Platforms (CMP) since the advent of the GDPR.
What began as simple binary consent (yes/no) has evolved into a sophisticated privacy-enhancing ecosystem. Modern CMPs like ours now orchestrate complex frameworks (TCF, GPP, Consent Mode), adapt to multiple jurisdictions, and provide dynamic privacy controls, evolving into foundational PETs that enable other privacy technologies to function effectively.
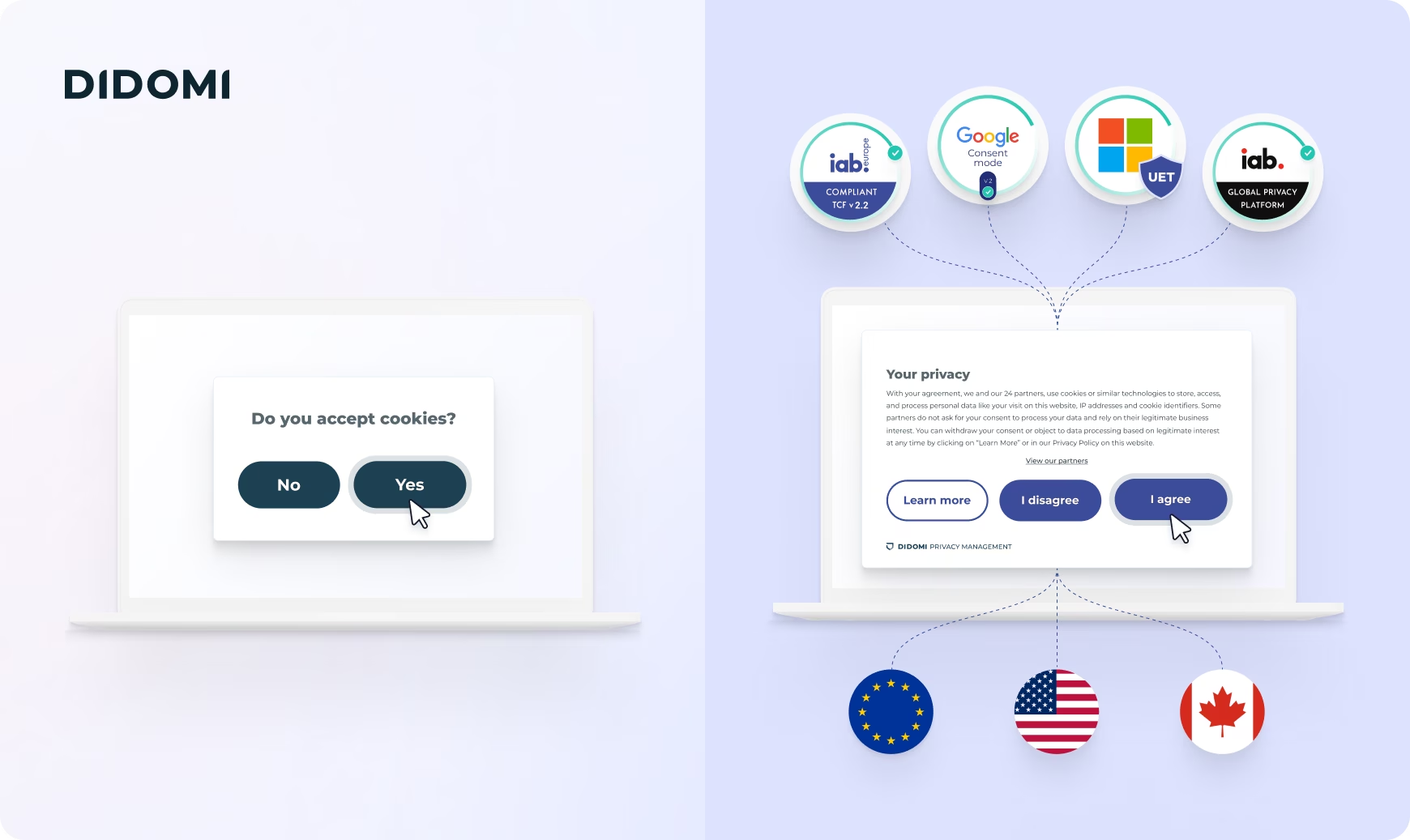
This evolution is accelerating as emerging technologies like AI, voice assistants, and virtual reality create new data touchpoints that require sophisticated consent orchestration. We expect consent management to become even more integral to the privacy ecosystem, and look forward to continuing to lead with cutting-edge technology answers to business challenges.
{{learn-more-about-our-cmp-solution}}
Examples of PETs
There are a myriad of PETs that organizations can utilize to help protect PII, enabling companies to maintain control over collected personal data while also mitigating potential privacy and security risks.

For example, if an organization is looking to bolster its consent management protocols, it could utilize Didomi’s multi-regulation consent management platform. For data vaults and PIMS, allowing users to store, manage, and share their data, reputable service providers include Solid Pods and Digi.me. For homomorphic encryption, top-notch service providers include Microsoft SEAL, Zama, IBM HELib, and others.
Below is an overview of different types of PETs and how they can be deployed:
Anonymization
Data anonymization is a PET that can effectively transform collected personal data by removing or obscuring personally identifying information.
Once anonymized, it would likely be impossible to link that data back to a particular individual. The objective of anonymization is to preserve the utility of collected personal data while strengthening its privacy and security.
Benefits of anonymization
Helps shield a data subject’s personal information, making them less identifiable and thereby enhancing overall data protection.
Confidential Computing
Confidential computing allows organizations to engage in data processing within secure enclaves.
For context, confidential computing helps protect sensitive data safely via isolation and remote attestation. Isolation helps protect sensitive data while it is in use. Remote attestation helps verify and validate this protection and how the data will be used prior to computation.
This strategy can help mitigate the risk of unauthorized access to data during computation, and provides enhanced security during data analysis and processing.
Benefits of Confidential Computing
Provides the ability to process and analyze personal data in a more secure computing environment.
Differential Privacy
Differential privacy is a mathematical method that deploys aggregation for the purposes of data analysis.
Differential privacy works by introducing randomness into query responses, making it more difficult for any one party, or parties, to identify personal data points. Specifically, differential privacy is focused on determining the precise amount of randomness that is necessary to achieve statistical privacy protection.
Benefits of Differential Privacy
Helps in balancing data analysis needs with enhanced privacy protections.
Differential Privacy Use Case
The U.S. Census Bureau utilized differential privacy during the 2020 Census to reduce the risk of re-identification of U.S. citizens who shared detailed demographic information, while still
allowing the federal agency to release aggregate statistics regarding the U.S. population.
Federated Learning
Federated learning is considered to be a decentralized approach to enhance machine learning.
In effect, a model is trained across multiple decentralized devices or servers that retain local data samples, without exchanging them. Rather than sending raw data to a central server, only model updates (also known as gradients) are communicated, which can help bolster the overall privacy protections of collected and processed personal data.
Benefits of Federated Learning
Provides the ability to collaborate with organizations to train AI models or engage in research projects without sharing or revealing sensitive personal data.
Synthetic Data
Synthetic data enables organizations to generate artificial data that mirrors real-world personal data, while still preserving important data privacy protections.
By using synthetic data, organizations can help safeguard sensitive PII by generating synthetic datasets. These synthetic datasets provide similar statistical qualities and features as real-world datasets while protecting private data points.
In effect, synthetic data can aid organizations in mitigating the risk of data exposure while conducting effective data analyses and developing machine learning models.
Benefits of Synthetic Data
Ability to conduct analysis without having to access or share actual user data.
Synthetic Data Use Case
American Express generated statistically accurate synthetic data from financial transactions to help conduct fraud detection and aid in the training of fraud detection models. Similarly, Waymo utilized synthetic data to develop realistic driving data sets to train its self-driving vehicle systems.
Homomorphic Encryption
Homomorphic encryption allows for computations to occur on encrypted data without having to engage in any decryption.
This can help organizations by ensuring data privacy while still engaging in meaningful data analysis with encrypted information.
Benefits of Homomorphic Encryption
Ability to process data in an encrypted state thereby retaining privacy protections for personal information.
Homomorphic Encryption Use Case
A collaboration between the Dana-Farber Cancer Institute and Duality Technologies, Inc., leveraged homomorphic encryption to develop impactful insights from multi-sourced, encrypted data without needing to decrypt the data. In effect, the deployment of homomorphic encryption allowed these organizations to work on large-scale genome-wide research studies while protecting sensitive health data.
Secure Multiparty Computation
Secure multiparty computation relies on cryptographic protocols involving encryption and mathematical techniques to enable multiple parties to jointly collaborate on computations involving personal data.
This strategy helps ensure that no party learns anything beyond the output of the computation.
Benefits of Secure Multiparty Computation
Ability to implement stringent access controls to ensure only authorized parties are able to access sensitive data, which empowers organizations to share information across different business units, as well as with third parties, while retaining a high level of data security.
Secure Multiparty Computation Use Case
Multiple counties in the United States leveraged secure multiparty computation to run sensitive queries involving incarceration status, usage of mental health facilities, and public housing benefits while ensuring that the input data (e.g., criminal records and mental health visit records) were kept strictly confidential to each party that shared this data.
Trusted Execution Environments
Trusted execution environments are secure hardware or software environments within a computer system. These environments provide a secure and isolated area for executing sensitive code or operations. They can be utilized to protect code and data within them from external tampering, even from the operating system or other software layers.
Benefits of Trusted Execution Environments
Helps manage how personal data is structured within particular environments to ensure access is controlled, while maintaining the integrity and confidentiality of sensitive personal data.
Trusted Execution Environment Use Case
Google’s secure Operating System (OS) for Android, known as Trusty, utilizes a trusted execution environment as a PET. Trusty and the Android OS run in parallel, with Trusty isolated from the rest of the system by both hardware and software. The isolation of Trusty helps protect the OS from getting impacted by malicious applications that a user may inadvertently install.
What are some of the benefits of PETs?
If an organization is conducting a cost-benefit analysis for the utilization of PETs, there are an array of potential benefits associated with deploying these technologies for personal data obtained via a user’s consent.
Considering the proliferation of digital technologies, organizations are being tasked with processing and maintaining a significant amount of personal data, including potentially sensitive data (e.g., financial data, health data, etc.).
The use of PETs can assist an organization in developing secure data processing protocols, maintaining data privacy, and ensuring compliance with U.S. and global data privacy regulations. Let’s explore some of these benefits in more depth.
Adherence to data minimization
Whether your organization is trying to comply with the EU’s General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), or a myriad of other U.S. consumer data privacy laws, a core principle of these regulatory frameworks is data minimization.
For context, data minimization obligates organizations to collect only the minimum amount of data that is absolutely necessary for a specified purpose. Utilizing PETs can help organizations to more efficiently and securely manage personal data without having to process and store unnecessary or excessive personal information.
Compliance with consumer data privacy regulations
In addition to strengthening adherence to data minimization, PETs can assist organizations in strengthening their compliance posture with an ever-expanding patchwork of consumer data privacy regulations.
These regulations routinely require organizations to implement specific security measures to help protect the personal data of consumers. PETs can play a key role in achieving compliance with the GDPR, CCPA, and other regulatory frameworks such as the Health Insurance Portability and Accountability Act (HIPAA), Gramm-Leach-Bliley Act (GLBA), and the Children's Online Privacy Protection Act (COPPA). In effect, the deployment of PETs can assist organizations in mitigating the risk of incurring legal penalties and substantial fines.
As an example of how PETs can help with regulatory compliance, consider healthcare providers. Within the health sectors, providers could utilize PETs for research-related data collaboration. The use of PETs could assist the healthcare provider in strengthening their compliance posture with the HIPAA, HITECH Act, and other medical data privacy regulations.
Enhanced protections for data collaboration
As indicated above, PETs can play a valuable role in assisting organizations with data collaborations. This is important because many organizations need to collaborate on matters with third parties (e.g., service providers, partners, research organizations, etc.) that may entail the sharing of personal data.
PETs, particularly secure multiparty computation and federated learning, can be utilized to ensure secure data collaboration without needlessly exposing sensitive personal information. If organizations can collaborate securely, it helps promote innovation and efficiency while also preserving data privacy.
An example of how PETs can be deployed for data collaboration can be found in multinational organizations with operations in the U.S., the EU, and other countries. Such an organization could utilize federated learning as a PET to aid in the training of an AI model that involves using data collected from different offices within the larger organization. With federated learning, each office could effectively process personal data locally on its devices while still contributing to the AI model’s update. This strategy would help ensure sensitive customer data does not need to cross borders and potentially trigger regulatory obligations associated with international data transfers.
Mitigating the risk of data misuse
By deploying PETs such as homomorphic encryption, organizations can reduce the risk of personal data being misused, sold, or inadvertently shared with unauthorized parties.
In effect, PETs can aid organizations in establishing protocols so personal data is only used for its intended purpose and only by authorized individuals within an organization.
What PETs mean for the digital marketing industry
As the digital ecosystem continues to evolve, marketing departments and advertisers are finding it more challenging to reach new audiences and measure the return on investment (ROI) of digital marketing efforts due to an ever-expanding patchwork of state consumer data privacy laws and federal regulations.
As indicated above, PETs can help marketing teams and advertisers achieve marketing utility from collected personal data while delivering data protection and privacy assurances to customers who have consented to share their personal information with an organization.
As the use of PETs proliferates, now is an opportune time for digital marketers to lean in and embrace the use of these innovative technologies.
For example, PETs are routinely being deployed and implemented on an array of tech platforms and other AdTech partners, which means digital marketing teams and advertisers will ultimately need to embrace and adopt these privacy-enhancing technologies.
A word of caution: PETs are not perfect
There are many benefits associated with using PETs in enhancing data privacy protections.
However, it is important to understand that PETs are not perfect and have some inherent limitations. For example, even though PETs are generally effective in protecting user privacy, they run the risk of reducing data utility for an organization. In addition, certain types of PETs can create challenges when it comes to implementing certain basic privacy principles, such as data transparency and the processing of data subject requests (e.g., right to know, right to erasure, right to correction, etc.).
These limitations are why over-reliance on PETs is not recommended. Rather, deploying PETs should be done in conjunction with other foundational security practices and protocols.
PETs are likely to play a larger role in data privacy going forward
The yuse of PETs by various organizations is growing rapidly and could become the industry standard in the near future.
Over the next 5 to 10 years, there is a realistic possibility that PETs become part of the default architecture for different types of software, services, and so forth. For example, new AI tools and applications are likely to require advanced controls over the use of personal data in large language models and how that data is processed. Data privacy could become a core component of basic AI architecture.
Considering the use of PETs is likely going to expand in the years ahead, organizations should consider taking proactive steps to integrate PETs into their data privacy protocols sooner rather than later.
How Didomi can help you get started with PETs
PETs can serve as a valuable tool in bolstering an organization’s data security posture, and Didomi is here to help.
Our solutions are designed to help address complex data privacy challenges, such as multi-regulation consent management and privacy governance, and address the need to provide self-service user privacy journeys and premium support services while adhering to top-level security standards.
We recently acquired Addingwell, a server-side tracking and tagging platform, and have joined forces with Sourcepoint, a data privacy technology pioneer with strong publisher market share and over 200 global enterprise customers. When you engage with Didomi, you’ll have access to solutions and services that bolster your overall data privacy compliance posture.
If you’re looking to implement PETs as a component of your data security program, please get in touch. We help organizations collect, store, and leverage user choices across multiple channels, increasing precision in marketing and advertising operations, and cultivating trust through transparent data practices:
{{talk-to-an-expert}}

.svg)













.avif)