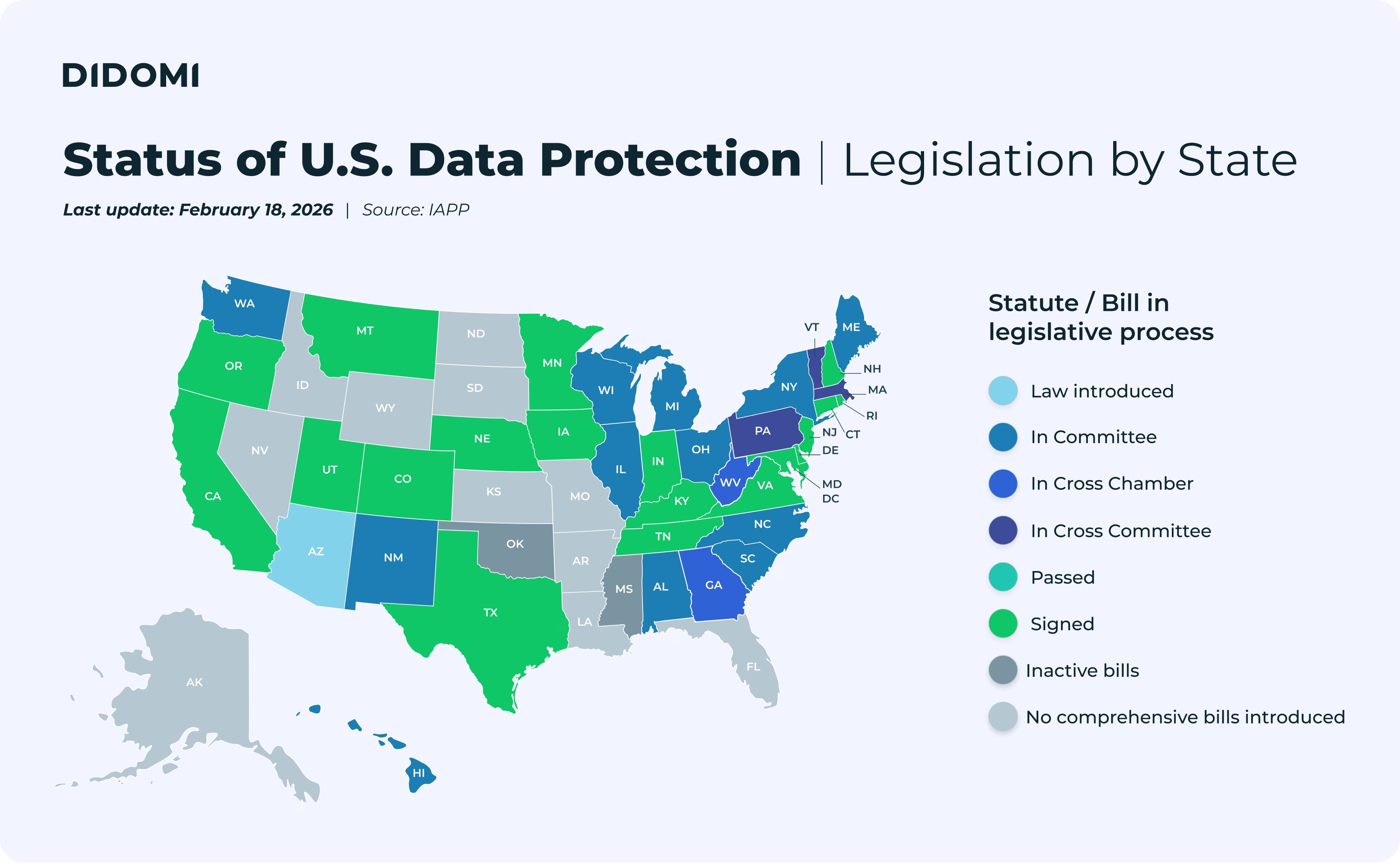
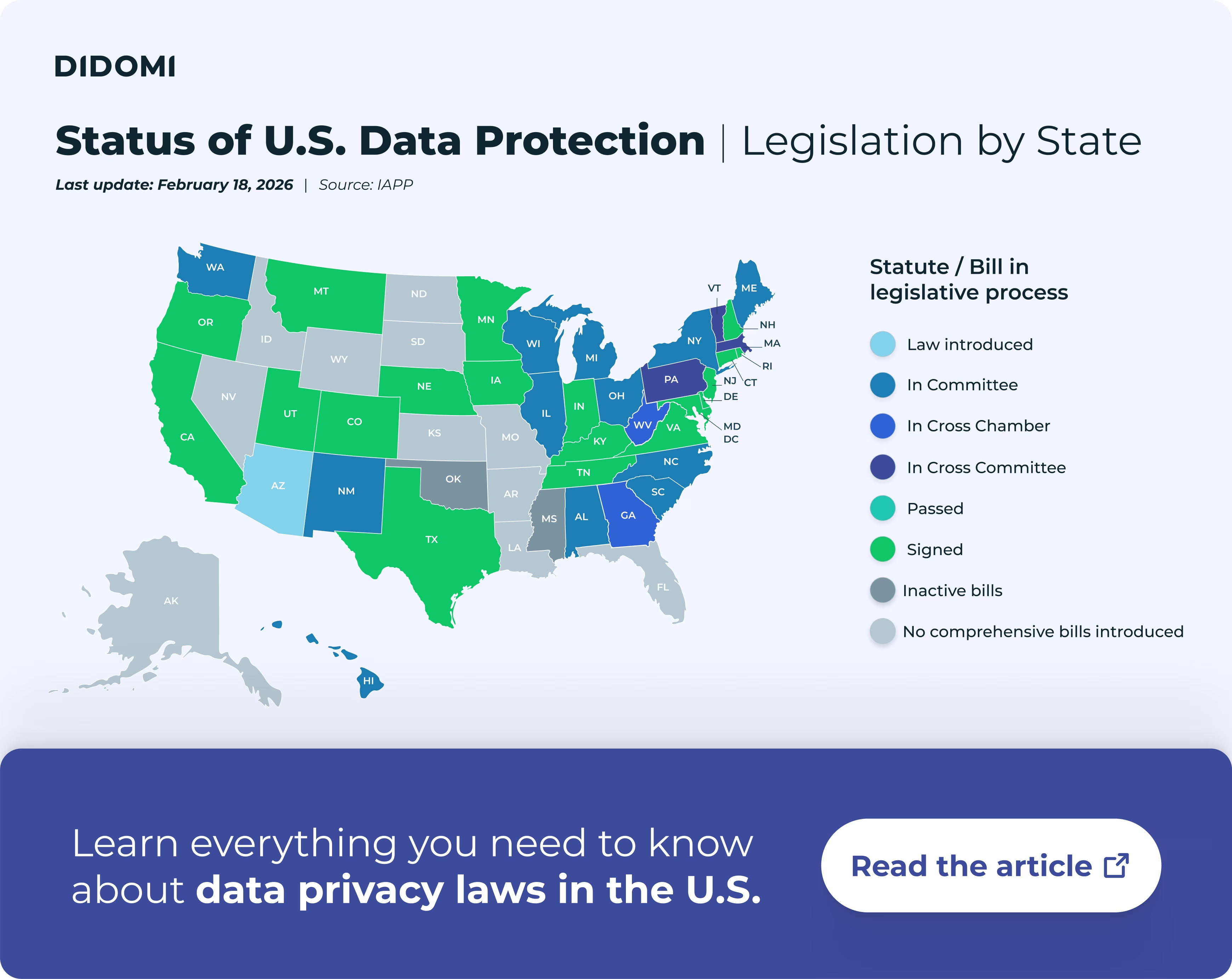
Since the advent of GDPR, user consent has been established as the primary legal basis for data collection. It has continued to become increasingly critical for digital operations, including in new, emerging regulations around the world (like in the U.S.).
However, even when organizations do everything right at the point of collection, two significant issues can arise later: consent string tampering and impact on website performance.
The hidden risks in the consent supply chain
In today’s digital ecosystem, the consent lifecycle doesn’t end at collection. Consent signals travel through internal systems, third-party tools, and the advertising supply chain. Along the way, two key risks can arise:
1. Consent String Tampering
Consent strings can be modified, spoofed, or duplicated as they pass through the advertising supply chain, often without detection. Since there’s no built-in way to verify whether a string was altered, organizations face serious challenges:
- They can’t reliably prove consent validity in audits or user complaints
- They’re exposed to regulatory enforcement and ad fraud
- They lose control over what should be a trustworthy signal of user choice
This is obviously a critical liability, with the potential to expose companies to legal risk and potential fraud.
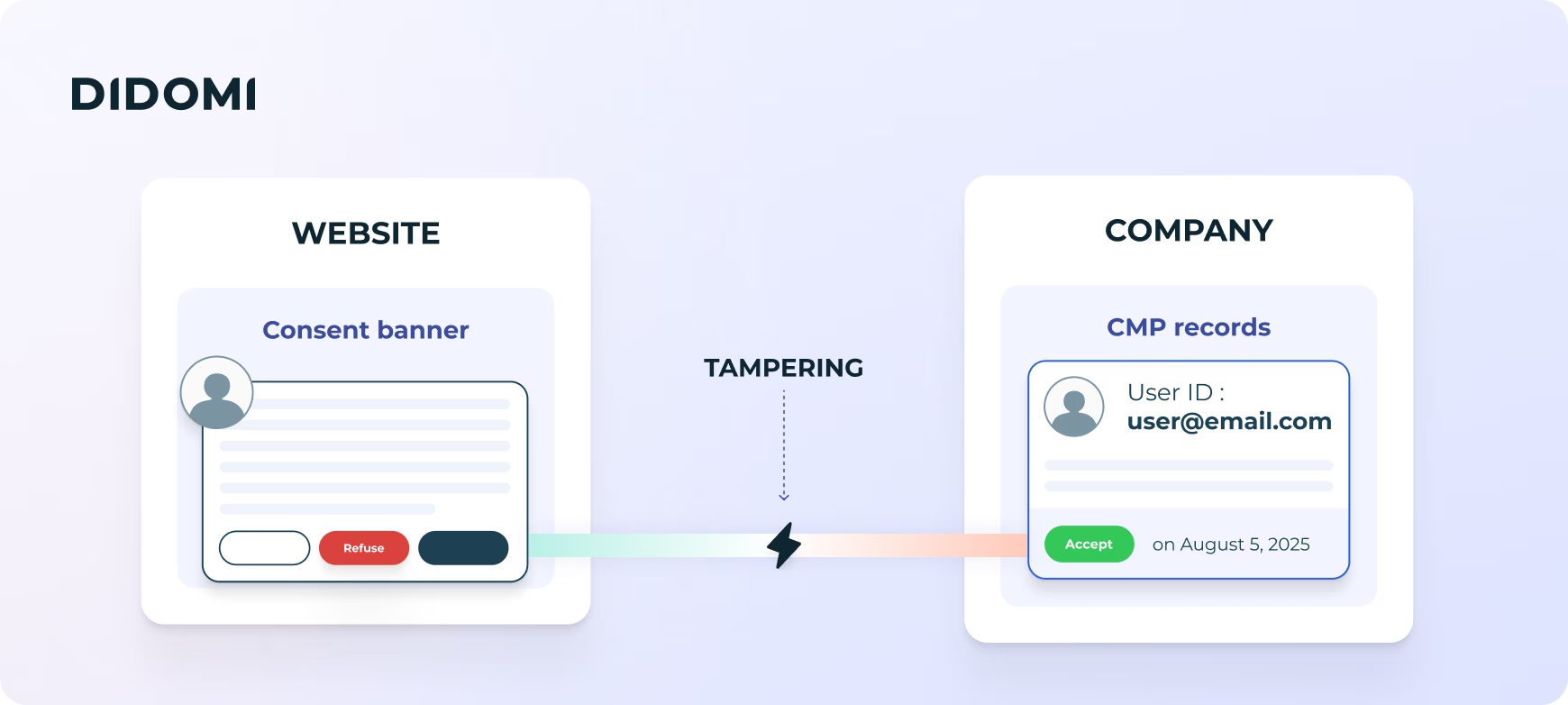
2. Large cookies and degraded performance
Current technologies often rely on JSON-formatted consent tokens, especially when dealing with custom vendors and granular purpose settings. This results in the following:
- Large cookie sizes that exceed browser limits
- Slower page loads that hurt SEO and frustrate users
- Increased processing costs and complexity behind the scenes
These impacts might be visible at first glance, but they create real friction for engineering, marketing, and compliance teams, and directly affect revenue.
Introducing tools to prevent consent string tampering and ensure consent integrity
To counteract these growing risks, Didomi has introduced two new features:
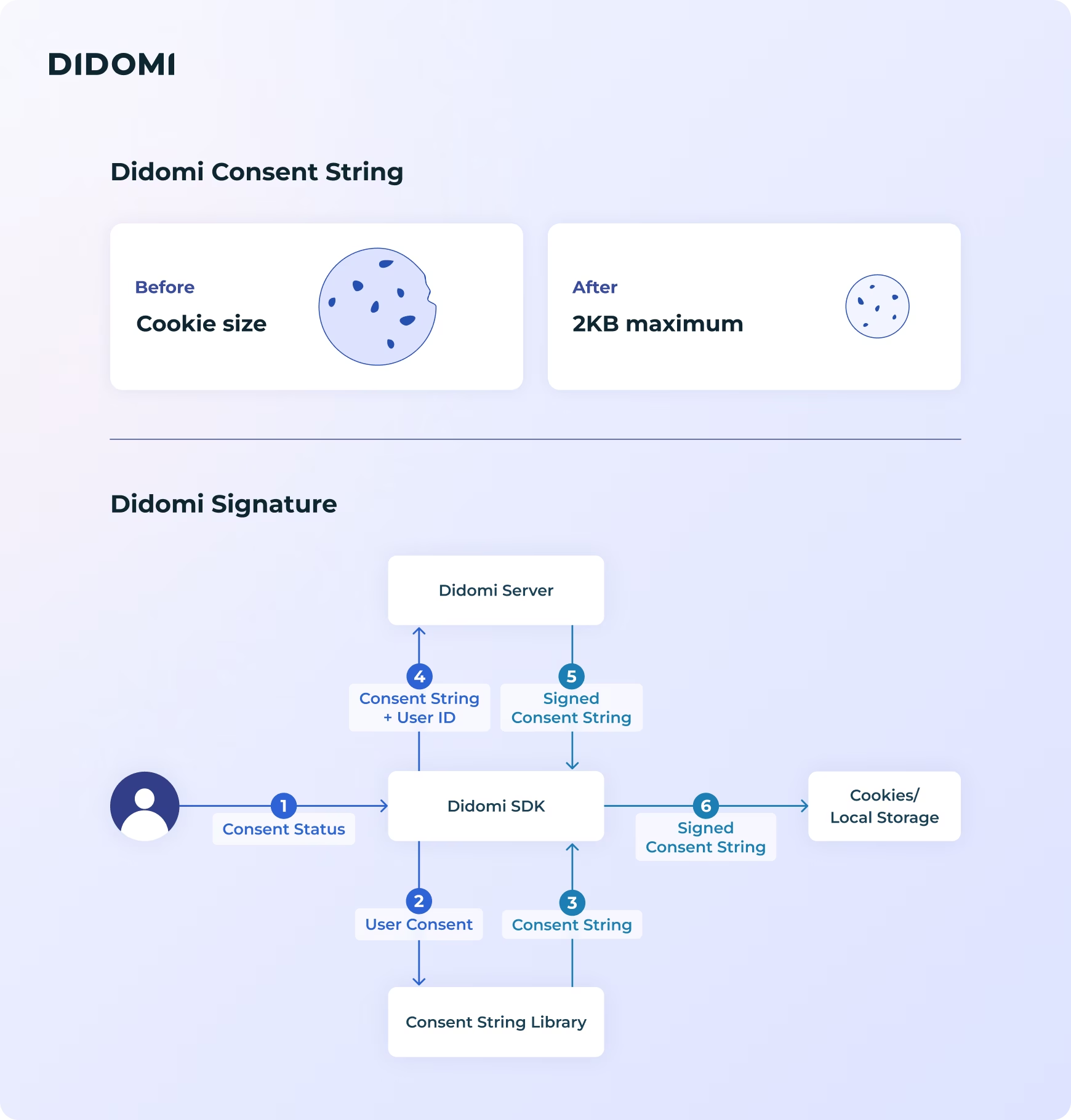
- Didomi Consent String (DCS) compresses consent strings into a lightweight binary format to improve performance and reduce backend load.
- Didomi Signature applies a cryptographic proof to each consent string, verifying that it is authentic and hasn’t been altered.
How does it work? The DCS is automatically encoded in the most efficient format to keep cookies under 2KB for maximum performance on both web and mobile., The Signature feature is applied server-side and travels with the consent string to prove its authenticity wherever it appears.
Together, they deliver tamper-evident, performance-friendly consent infrastructure that can scale across enterprise environments.
This is particularly relevant for a range of organizations and use cases:
- Global brands preparing for internal audits or regulatory reviews that demand clear, verifiable records
- Publishers looking to improve site performance and data security.
- Companies preparing for audits or regulatory reviews.
- Adtech platforms that need to verify consent before bidding, targeting, or storing user data
- Privacy and compliance teams who want to simplify backend workflows and reduce risk
- Product and engineering teams working to optimize data handling and processing at scale
- Companies operating in non-GDPR markets where cookies tend to be larger and performance concerns are even more pronounced.
We built DCS and Signature to give our customers what the industry was missing: a simple, verifiable way to prove consent integrity without slowing anything down. It’s a meaningful step forward for both performance and trust.
- Jeff Wheeler, VP of Product at Didomi
To learn more about the Didomi Consent String and Signature features, check out our technical documentation or book a call with the team to see if this could be relevant to your business:
{{talk-to-an-expert}}

.svg)












.png)